HTB CTF Write-up: Cargo Delivery
Cargo Delivery was a Python command line application that uses AES CBC encryption and is vulnerable to a padding oracle attack.
The HTB x Uni CTF 2020 - Qualifiers have just finished and I wanted to write-up some of the more interesting challenges that we completed.
As with several of the challenges the server source code was available so that you could develop the exploit locally.
Summary
Cargo Delivery was a Python command line application that uses AES CBC encryption and is vulnerable to a padding oracle attack.
Walk-Through
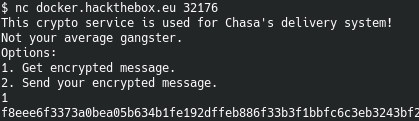
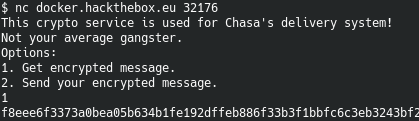
The interface to this challenge presents two options: 1. Get an encrypted message (the flag) or 2. Send an encrypted message.
This corresponds to the main loop of the Python application and is shown below:
def challenge(req):
req.sendall(bytes('This crypto service is used for Chasa\'s delivery system!\n'
'Not your average gangster.\n'
'Options:\n'
'1. Get encrypted message.\n'
'2. Send your encrypted message.\n', 'utf-8'))
try:
choice = req.recv(4096).decode().strip()
index = int(choice)
if index == 1:
req.sendall(bytes(encrypt(flag) + '\n','utf-8'))
elif index == 2:
req.sendall(bytes('Enter your ciphertext:\n', 'utf-8'))
ct = req.recv(4096).decode().strip()
req.sendall(bytes(is_padding_ok(bytes.fromhex(ct)), 'utf-8'))
else:
req.sendall(bytes('Invalid option!\n', 'utf-8'))
exit(1)
except:
exit(1)
By inspecting the is_padding_ok function it becomes apparent that the app will return an error when the padding is incorrect in the provided ciphertext.
def is_padding_ok(data):
if decrypt(data) is not None:
return 'This is a valid ciphertext!\n'
else:
return 'Invalid ciphertext\n'
At first glance this may not seem interesting, but it can be used to to perform a padding oracle attack and decrypt the ciphertext one byte at a time.
I wrote a short bit of Python using pwntools that will automatically connect to the server and grab a copy of the ciphertext:
This gives the flag for this challenge:
HTB{CBC_0r4cl3}

